Navigating the Cyber Labyrinth: Our Holistic Approach to Security Consulting
In today's hyper-connected world, the cyber threat landscape is more complex and dynamic than ever. Businesses face a relentless barrage of sophisticated attacks, making robust cyber security not just an IT concern, but a fundamental business imperative. At Scardina Cyber Consulting, we understand that effective cyber security is not achieved through a single solution, but through a comprehensive, integrated strategy. Our consulting approach is built upon the proven triad of People, Process, and Technology, ensuring a resilient and adaptive security posture for your organization.
The Foundation: People, Process, and Technology
True cyber resilience extends beyond firewalls and antivirus software. It requires a harmonious blend of empowered individuals, well-defined procedures, and strategically implemented technologies. Neglecting any one of these pillars leaves an organization vulnerable.
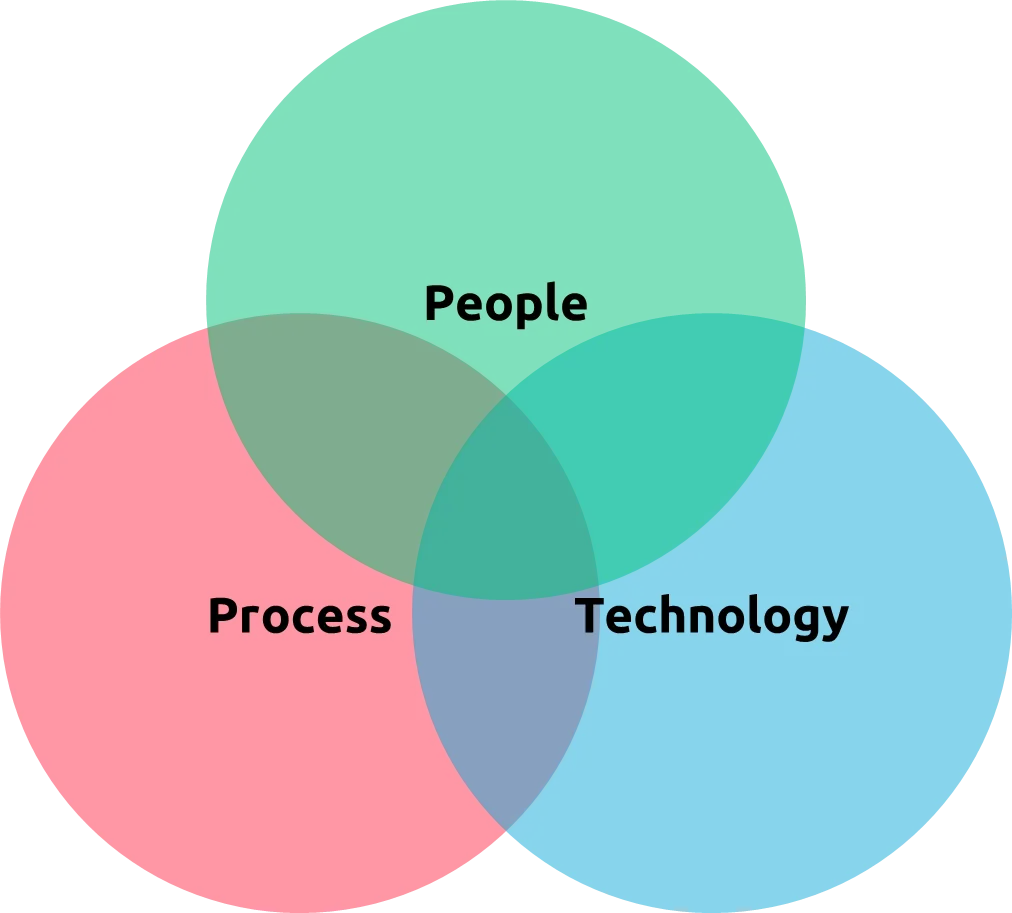
Let's delve into how we address each critical component:
1. People: The Human Element of Cyber Defense
Often cited as the weakest link, your people can, with the right empowerment, become your strongest line of defense. Human error, whether through accidental clicks or misunderstanding security protocols, is a leading cause of breaches. Our approach focuses on transforming your workforce from a potential liability into a vigilant asset.
Security Awareness & Culture:
We develop and help implement comprehensive security awareness training programs tailored to your organization's specific risks and employee roles. This goes beyond annual refreshers to foster a pervasive security-first culture where every employee understands their responsibility in protecting company assets.
Role-Based Training & Skill Development:
Not all employees face the same risks or require the same level of technical understanding. We design targeted training for technical staff (IT, security teams) to enhance their skills in threat detection, incident response, and secure system administration, while providing general staff with practical guidance on topics like phishing, social engineering, password hygiene, and secure data handling.
Executive Buy-in & Governance:
Leadership commitment is crucial. We work with your executive team to ensure they understand the cyber risk landscape, their role in governance, and the importance of championing security initiatives throughout the organization.
Incident Response Team Preparedness:
We assist in identifying and training key personnel to form an effective incident response team, ensuring they are prepared to act decisively when a security event occurs.
Our People-centric services aim to:
- Reduce human error and susceptibility to social engineering.
- Foster a proactive security culture.
- Equip your teams with the necessary knowledge and skills.
- Ensure clear lines of responsibility and accountability.
2. Process: The Framework for Resilient Operations
Even the most skilled people and advanced technology will falter without well-defined, repeatable, and adaptable processes. Strong processes provide the roadmap for consistent security practices, effective incident management, and continuous improvement.
Risk Assessment & Management:
We begin by understanding your unique business environment, critical assets, and specific threats. Our comprehensive risk assessments identify vulnerabilities and quantify potential impacts, allowing us to prioritize mitigation efforts effectively.
Policy & Governance Development:
Clear, actionable, and enforceable security policies are the bedrock of a strong security program. We help you develop or refine policies covering acceptable use, data classification, access control, incident response, disaster recovery, and more, ensuring they align with business objectives and regulatory requirements.
Incident Response & Business Continuity Planning (IRP/BCP):
We don't just plan for prevention; we prepare you for the "when," not "if." Our consultants work with you to develop robust IRPs and BCPs, ensuring minimal disruption and swift recovery in the event of a security incident or disaster. This includes tabletop exercises and simulations to test and refine these plans.
Compliance & Regulatory Adherence:
Navigating the complex web of regulations (e.g., GDPR, HIPAA, PCI DSS, ISO 27001) can be daunting. We provide expert guidance to help you understand your obligations and implement the necessary controls to achieve and maintain compliance.
Continuous Monitoring & Improvement:
The threat landscape is ever-evolving, and so too should your security processes. We help establish frameworks for ongoing monitoring, regular audits, and periodic reviews to ensure your security posture remains effective and adapts to new challenges.
Our Process-driven solutions ensure:
- A clear understanding of your cyber risk profile.
- Robust governance and actionable policies.
- Preparedness for security incidents and business disruptions.
- Adherence to relevant regulatory and compliance mandates.
- A culture of continuous security improvement.
3. Technology: The Tools to Empower Security
Technology is a critical enabler of a strong security posture, providing the tools to detect, prevent, respond to, and recover from cyber threats. However, technology alone is not a silver bullet. It must be strategically selected, correctly configured, and integrated effectively with your people and processes.
Strategic Technology Selection & Architecture:
We help you navigate the crowded marketplace of security solutions. Our vendor-agnostic approach focuses on identifying and implementing technologies that are fit-for-purpose, scalable, and integrate seamlessly into your existing infrastructure, aligning with your specific risk profile and budget. This includes designing defense-in-depth architectures.
Advanced Threat Detection & Prevention:
We leverage our expertise in areas like Security Information and Event Management (SIEM), Endpoint Detection and Response (EDR), Intrusion Detection/Prevention Systems (IDS/IPS), firewalls, and anti-malware solutions to build a multi-layered defense.
Data Protection & Encryption:
Protecting sensitive data, both at rest and in transit, is paramount. We advise on and help implement robust encryption, data loss prevention (DLP) strategies, and secure data storage solutions.
Vulnerability Management & Penetration Testing:
Proactively identifying and remediating weaknesses is key. We conduct thorough vulnerability assessments and penetration tests to simulate real-world attacks, uncovering potential entry points before malicious actors do.
Cloud Security & Identity Management:
As organizations increasingly adopt cloud services, securing these environments and managing digital identities effectively becomes crucial. We provide expertise in cloud security best practices, access controls, and identity and access management (IAM) solutions.
Our Technology-focused consulting delivers:
- Optimized security technology investments.
- Robust defense-in-depth architectures.
- Enhanced threat visibility and response capabilities.
- Protection for your critical data and systems.
- Proactive identification and remediation of vulnerabilities.
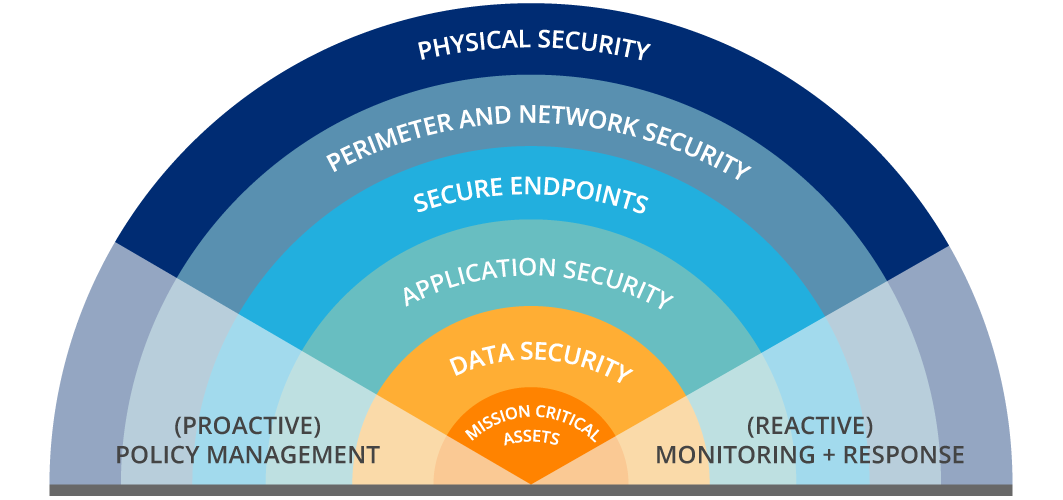
The Scardina Cyber Consulting Difference: Partnership and Tailored Expertise
At Scardina Cyber Consulting, we don't believe in one-size-fits-all solutions. We partner with you to understand your unique business context, challenges, and objectives. Our seasoned consultants bring a wealth of experience across diverse industries, applying the People, Process, and Technology framework to develop a cyber security strategy that is not only robust but also practical and aligned with your organizational goals.
We empower your organization to build a sustainable security posture that protects your assets, maintains customer trust, and enables business growth in an increasingly hazardous digital world.
Ready to strengthen your defenses? Contact us today for a consultation and discover how our holistic cyber security approach can safeguard your future.